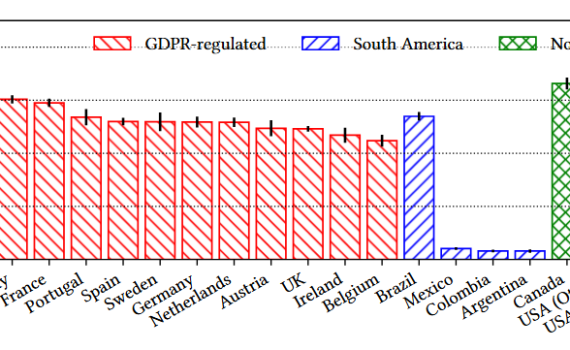
In the following post, we offer the data and the code to replicate the figures regarding CMP adoption included in the paper “Consent Management Platforms: Growth and Users’ Interactions over Time“, currently under revision. In summary, the paper shows how Consent Management Platforms have become popular in the last 9 […]
Open Datasets & Libraries
Precis: a concise summary of essential points, statements, or facts Info This webpage contains additional material on the paper: LogPrecis: Unleashing Language Models for Automated Malicious Log Analysis Abstract Security logs are the key to understanding attacks and diagnosing vulnerabilities. Often coming in the form of text logs, their analysis […]
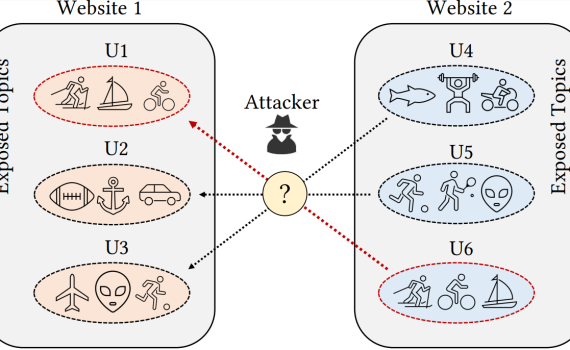
Author: Nikhil Jha Third-party cookies have been a core pillar in Interest-Based Advertising (IBA). Their use allowed advertisers to build profiles of users surfing the web, in order to offer them advertisements tailored to their interests.Privacy advocates have long criticized the use of third-party cookies, forcing legislators to take action, […]
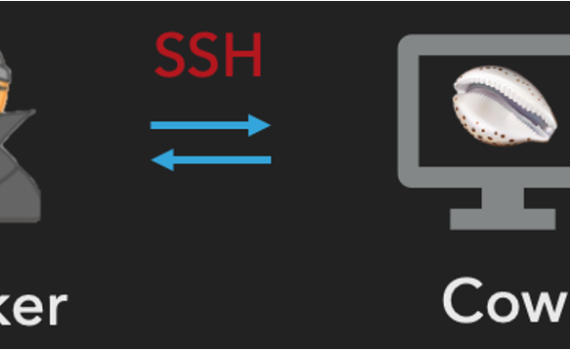
This webpage contains additional material on the paper: “Towards NLP-based Processing of Honeypot Logs” Published in: 2022 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) The data You can find the data on this link: Cowrie_Data Each line represents an interaction between Cowrie and the attacker. The column “session_id” […]
This webpage contains additional material on the paper: “Where did my packet go? Real-time prediction of losses in networks” Currently under revision The data You can find the dataset on this link: RTP traffic losses data where the column “lossOrNot” is the target variable, the column “num_packet_loss” is the number […]
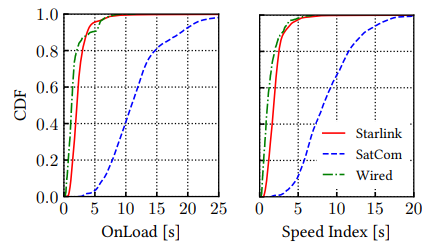
In this webpage, you can find the dataset we used in the paper: “A First Look at Starlink Performance” François Michel, Martino Trevisan, Danilo Giordano, Olivier Bonaventure. To Appear on the 2021 ACM Internet Measurement Conference. Summary With new Low Earth Orbit satellite constellations such as Starlink, satellite-based Internet access […]
This repository contains data and information regarding the papers: L. Vassio, M. Garetto, C. Chiasserini, and E. Leonardi. Temporal Dynamics of Posts and User Engagement of Influencers on Facebook and Instagram. 2021 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM), 2021. DOI: 10.1145/3487351.3488340 L. Vassio, M. […]
This repository contains data and information regarding the paper: F. Bertone, L. Vassio, and M. Trevisan, “The Stock Exchange of Influencers: A Financial Approach for Studying Fanbase Variation Trends” Proceedings of the 2021 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, 2021, 0.1145/3487351.3488413 Download paper Download presentation […]
This page collects the open datasets and code used in the papers: L. Vassio, D. Giordano, M. Trevisan, M. Mellia, A.P.C. da Silva. Users’ Fingerprinting Techniques from TCP Traffic. ACM SIGCOMM Workshop on Big Data Analytics and Machine Learning for Data Communication Networks, Los Angeles, USA, pp. 49-54, 2017. DOI: […]
Introduction ODySSEUS is a data management and simulation software for mobility data, focused mostly on shared fleets in urban environments. Its goal is to provide a general, easy-to-use framework to simulate shared mobility scenarios across different cities using real-world data. Internally, it makes use of several open-source Python libraries such […]
This webpage contains additional material of the paper: “Real-Time Classification of Real-Time Communications“ Published in IEEE Transactions on Network and Service Management, July 2022 Authors: Gianluca Perna, Dena Markudova, Martino Trevisan, Michela Meo, Paolo Garza, Maurizio Munafò, Giovanna Carofiglio The data You can find the dataset and the classifiers on […]
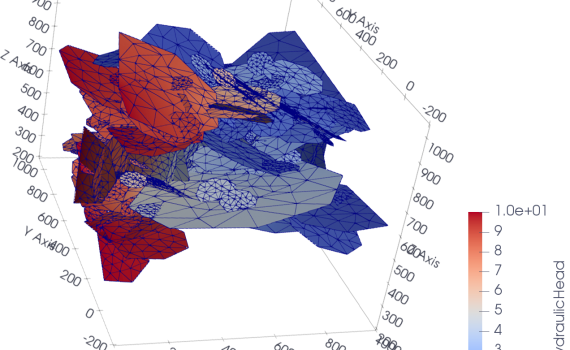
This repository contains data and information regarding the paper: Stefano Berrone and Francesco Della Santa, “Performance Analysis of Multi-Task Deep Learning Models for Flux Regression in Discrete Fracture Networks” (to appear on the special issue “Quantitative Fractured Rock Hydrology” of Geosciences, ISSN 2076-3263). Summary: Analysis of underground flows in fractured […]